Success in the SaaS (Software as a Service) industry depends on building customer-centric products and designing a sales organization that balances skills, processes, and tools to deliver measurable value.
A true SaaS-driven organization thrives on self-organization and self-learning — enabling teams to adapt quickly, make data-driven decisions, and continuously innovate. In this dynamic environment, there’s always a trade-off between the number of customers willing to subscribe, how much they are willing to pay, and consequently, how experienced and costly your sales team can be. Striking the right balance between these factors is crucial for sustainable growth.
Over the last decade, SaaS products have dramatically outpaced traditional software models. This shift is driven by the SaaS model’s ability to deliver “value for customers” rather than merely offering a service. Successful SaaS companies achieve this by:
- Acquiring customers faster through shorter sales cycles and frictionless onboarding.
- Reducing redundant features and operational costs through data-backed product optimization.
- Innovating rapidly with shorter customer feedback loops and agile delivery.
- Driving growth through smarter product packaging, dynamic pricing, and upselling opportunities.
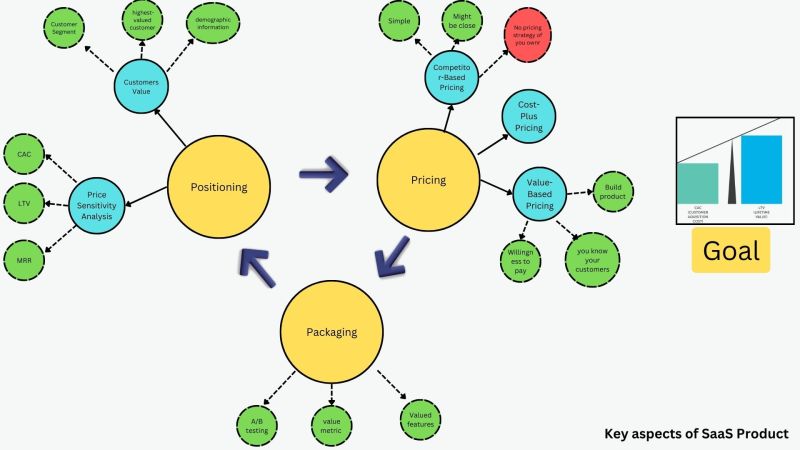
To build and scale a successful SaaS product, organizations must focus on several key aspects:
- Customer-Centric Product Design
- Understand customer problems deeply and design intuitive, outcome-oriented solutions.
- Prioritize simplicity, usability, and measurable value over feature overload.
- Data-Driven Decision Making
- Leverage usage analytics, customer feedback, and LLM-based insights to guide product evolution.
- Use data to identify friction points in onboarding, retention, and conversion.
- Self-Organizing and Learning Teams
- Empower cross-functional teams to make decentralized decisions.
- Foster a culture of continuous learning, experimentation, and accountability.
- Sales and Customer Success Alignment
- Build sales processes that emphasize understanding customer needs over transactional selling.
- Align customer success and product teams to ensure continuous value delivery post-sale.
- Scalable Architecture and Automation
- Design with scalability, reliability, and security in mind from day one.
- Automate repetitive processes — from deployment to billing and support.
- LLM-Driven SaaS Intelligence
- Integrate LLM models to automate customer support, personalize product recommendations, and improve onboarding.
- Use AI to analyze customer behavior, predict churn, and suggest retention strategies.
- Continuously refine business insights, product documentation, and training using generative models.
Key Aspect of Platform Design
- Self serving
- Provide configurable features
- Be generic , but flexible to be customisable
- Fast release cycle
- Automated testing
- Adopt iterative process
- Build real time tracking and monitoring system
Technical Consideration : API development
Any business capability that you want to expose to a consumer (internal or external) can be considered an API.Exposing such business capabilities in a way that you cancreate, manage, secure, analyze, and scale them, is known as API management

Key Architectural Components — Modern API-First SaaS Platform
Below is a clear, action-oriented description of each architectural component you listed, plus responsibilities, design considerations, LLM integration opportunities, operational notes, and useful success metrics. Treat this as a single-page reference to include in your architecture or product playbook.
API Gateway
Purpose: Single entry point for all external API traffic. Handles routing, authentication, rate limiting, request validation, and basic observability.
Responsibilities
- Request routing and protocol translation (HTTP/1.1, HTTP/2, gRPC, WebSocket)
- Authentication & authorization (JWT, OAuth2, mTLS)
- Rate limiting / throttling and burst control
- Request/response transformations (headers, payload shapes)
- Centralized logging and metrics export (to Prometheus/Datadog/etc.)
- Failover and basic traffic shaping
Design considerations
- Keep it stateless; use external stores for policies and quotas.
- Use short config-refresh windows for policy updates.
- Offload heavy tasks (e.g., complex auth checks) to dedicated services.
LLM opportunities
- Generate adaptive error messages / developer help on-demand.
- Auto-document API changes and generate migration guides.
- Provide interactive API troubleshooting assistants in the developer portal.
Success metrics
- 99.9% availability, request latency P95/P99, throttled vs allowed requests, auth failures.
API Store / Developer Portal
Purpose: A discoverable, self-service hub for internal and external developers to find, try, and consume APIs.
Responsibilities
- API catalog with versioning and change logs
- Interactive API docs / Try-it consoles (Swagger / OpenAPI)
- API key / client credential provisioning and usage dashboards
- SDK generation and sample apps
- Subscription plans and usage quotas (linked to monetization)
Design considerations
- Expose clear SLAs and version migration paths.
- Provide postman/SDKs and code samples for major languages.
- Integrate single sign-on (SSO) and role-based access for enterprise consumers.
LLM opportunities
- Natural language search across docs and examples.
- Auto-generated SDK snippets and sample code tailored to the user’s context.
- Conversational onboarding assistant for new API consumers.
Success metrics
- Onboarding time (minutes to first successful call), docs usage, developer satisfaction (NPS).
Security, Caching, Throttling, etc.
This is a cross-cutting set of capabilities that must be enforced consistently.
Security
- Authentication (OAuth2, OpenID Connect), Authorization (RBAC/ABAC)
- Transport security: TLS everywhere; support for mTLS for service-to-service
- Secret management (vaults), key rotation policies
- Input validation, JSON schema enforcement, WAF rules for OWASP threats
- Audit logging and tamper-resistant event stores for compliance
Caching
- Edge caching (CDN) for static or cacheable API responses
- Distributed caches (Redis / Memcached) for application caches and session data
- Cache invalidation strategies and TTL governance
- Cache warming and shard awareness in multi-region deployments
Throttling / Quotas
- Per-user, per-client, per-endpoint quotas with burst windows
- Graceful degradation patterns and informative 429 responses
- Dynamic throttling policies based on system load or SLAs
LLM opportunities
- Intelligent anomaly detection for security events via LLM-enhanced classifiers.
- Auto-explainers for security incidents and remediation playbooks.
- Personalized cache and quota recommendations based on usage patterns.
Success metrics
- Security incidents, mean time to detect (MTTD) and respond (MTTR), cache hit ratio, quota violation rate.
API Monetization
Purpose: Turn APIs into a revenue stream or usage-based internal chargeback mechanism.
Responsibilities
- Plan and tier definitions (free, freemium, paid, enterprise)
- Metering and rating (per call, per data volume, per feature)
- Billing integration (invoicing, Stripe/Adyen, enterprise contracts)
- Usage dashboards and alerts for consumers
- Entitlement enforcement (what each plan allows)
Design considerations
- Decouple metering from enforcement for resilience (buffer/queue designed)
- Provide clear usage limits and near-real-time reporting
- Support trial accounts and soft limits for conversions
LLM opportunities
- Personalized pricing recommendations and ROI calculators for prospects.
- Auto-generated billing queries and human-readable invoice explanations.
Success metrics
- ARR/MTU by API, conversion rate (trial → paid), average revenue per user (ARPU), churn by plan.
Service Mesh
Purpose: Provide reliable, observable, and secure service-to-service communication in microservice architectures.
Responsibilities
- Service discovery, traffic routing, and A/B / canary deployments
- mTLS between services, fine-grained policy enforcement
- Outlier detection, circuit breaking, retries, and timeouts
- Distributed tracing and telemetry propagation (OpenTelemetry)
- Traffic mirroring and JWT propagation for security context
Design considerations
- Evaluate sidecar vs. eBPF approaches for latency and resource costs.
- Choose a mesh that supports multi-cluster and multi-region topologies if required.
- Keep platform policy management declarative and versioned.
LLM opportunities
- Summarize distributed traces and suggest root causes.
- Auto-generate service-level runbooks and incident playbooks from historical incidents.
- Natural language routing rules or policies authored and validated by LLMs.
Success metrics
- Service success rate, interservice latency P95/P99, error budget burn, tracing coverage.
Cross-Cutting Operational & Governance Notes
- Observability: Centralize metrics, logs, and traces. Use OpenTelemetry. Provide dashboards for API health, business KPIs and SLOs.
- SLA/SLOs: Define SLOs per API and expose SLO status in the developer portal.
- Versioning & Backwards Compatibility: Adopt semantic API versioning, deprecation notices, and automated migration guides.
- Multi-Region / Resilience: Design for active-active or active-passive depending on RTO/RPO requirements.
- Compliance & Data Privacy: Data residency, consent management, PII masking, and encryption at rest/in transit.
- DevX & Platform: Provide CI/CD templates, contract tests, and a staging sandbox for partners.
Example Integration Pattern (how components work together)
- Client → CDN / API Gateway (auth, throttling)
- Gateway routes to public endpoints or to an internal API (service) via Service Mesh
- Service Mesh connects microservices; sidecars enforce mTLS and telemetry
- Business logic uses caches and backing stores; metrics emitted to observability stack
- Usage events feed the monetization engine and billing pipeline; alerts for quota breaches sent to portal
- Developer Portal + LLM assistants provide docs, SDKs, and conversational support
Quick Checklist for Implementation
- API OpenAPI/Swagger first; auto-generate docs and contracts
- Deploy a hardened API Gateway (stateless) with RBAC + quotas
- Provide Developer Portal with interactive docs and key provisioning
- Instrument everything with OpenTelemetry; central observability stack
- Deploy a Service Mesh for interservice security and traffic control
- Implement centralized secret & policy management (Vault, IAM)
- Build a resilient metering pipeline for monetization (event buffering + idempotency)
- Define SLOs and error budgets; expose them publicly to consumers
- Add LLM layers for docs, insights, anomaly summarization, and conversational help

Leave a Reply